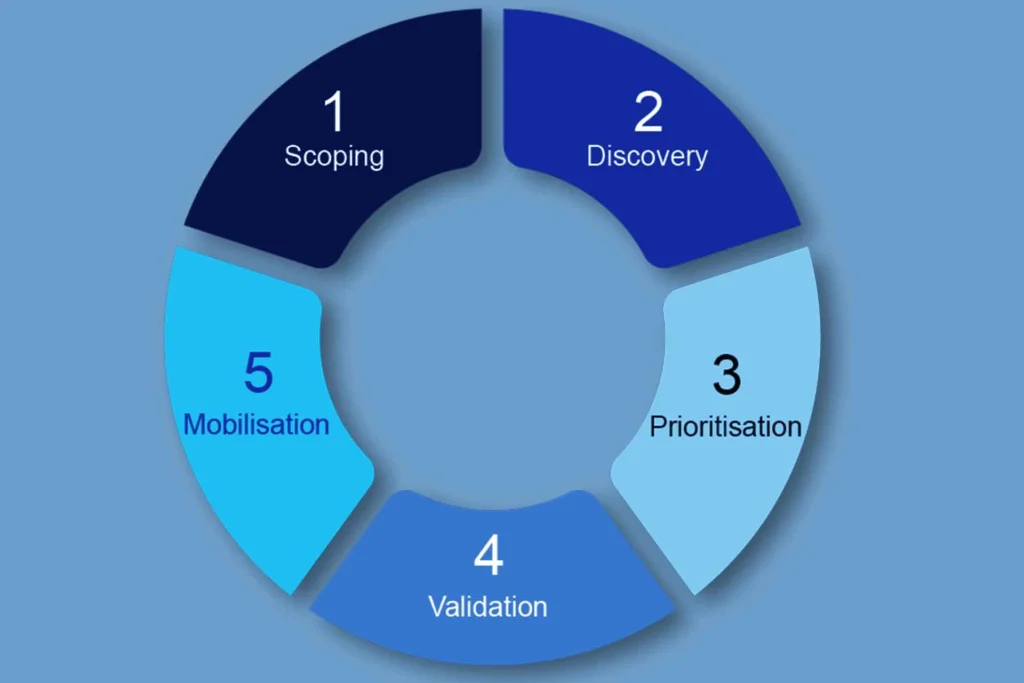
CTEM is a pragmatic approach to changing the entire IT security methodology, from onboarding new technology, people, and processes through asset decommissioning and departing employees. The CTEM program is a continuous cycle across the entire business, where validation and testing continuously identify, prioritise, validate, and remediate potential threats as they arise.
Before embarking on a CTEM program, many organisations will be moving from a ‘stop-start’ approach to security, where attention is pulled to daily issues that mean security teams are missing the big picture. CTEM helps you streamline your everyday tasks and keeps your people focused on the most important issue at the right time.
Proactive risk management and effective threat prioritisation provide a substantial benefit for security posture while also minimising compliance pressures. The actionable insights you gain, all aligned with key business objectives, mean you can be adaptable to changing compliance requirements while increasing the overall value of cybersecurity efforts.